Credit is important to many frequent flyers who rely on travel credit cards to fuel and fund their travel needs. This week Equifax, one of three credit reporting bureaus in the US, announced the discovery of a data breach to their customer files. While the company seemed to have a plan in place, it became clear this week that their response was quite amateur in fact. But did the credit giant put even more customers in jeopardy through their response?
If you are considering booking travel or signing up for a new credit card please click here. Both support LiveAndLetsFly.com.
If you haven’t followed us on Facebook or Instagram, add us today.
Investigation and Breach
News this week broke about the data breach that happened over an extended period from mid-May through July and purportedly only affected those who had a credit dispute. I mentioned my own credit reporting issue as a result of Capital One accepting a charge after I closed my account, but failed to report that I had to call in to file the dispute as the website wasn’t processing my request.
In retrospect this seems quite obviously to be a consequence of the data breach. The site said nothing at the time of my filing, however, that there had been a breach. It wasn’t yet public information, though by the time I had filed Equifax not only knew of the breach but had completed their investigation, took down the ability to file disputes online, but still waited to tell customers like me, entrusting the company with further personal information.
It feels pretty slimy and maybe careless.
Prepared Response
Lessons learned from the Sony Playstation and Target hacks provide a standard script.
- Inform the public
- Offer free identity protection to possible affected parties
- Disclose as much as possible
- Enlist an outside specialist to secure systems
Following that model precisely, Equifax has done just that. In this website they setup solely for the purpose of this process, the brand outlines their initiatives. It serves as a notice to the public though the company also reached out to media, and I citedCNN in my post.
It also shouldn’t be any surprise (and practically no out-of-pocket cost) for the credit bureau and identity protection company to offer free protection to those affected. This is literally the least they could do, the very least. In fairness it is probably the service most desired by victims of the breach, but it is also like IHOP giving out free pancakes to customers that may have been harmed as a result of doing business with the brand. Other than the loss of those customer’s identity protection business, it’s not a big ask for Equifax to provide this to the victims.
While Equifax disclosed some of the information they have garnered, they still left far too much out. For example, here are some simple questions that still remain for me:
- If only 209,000 customers were possible affected, why are 143 million at risk?
- How did this happen? Assuming that the security experts have closed the entrance, can Equifax not now disclose what happened?
- Why can’t customers immediately protect themselves? You have to wait until an appointed day to officially register for your free protection. Which is provided by Equifax… why?
Rollout of the Response
So bad. If you’re a business that protects sensitive private data, you should have an ironclad plan for what would happen if there was a breach. Other companies have drills for cyber threats and don’t hold nearly the same level of sensitive personal information as Equifax, other companies have a better plan.
This came across as really quite amateur and that scares me to death. I don’t get to determine whether or not Equifax gets to manage my personal data in the future even though they can’t handle it in the present. A series of their mistakes in this rollout suggest that leadership for the business is approaching this in a cavalier manner despite their words to the contrary.
Original language suggested that by accepting the identity protection services, victims would forgo their right to bring suit against Equifax. They have since clarified this position on their website in all caps remarking:
“NO WAIVER OF RIGHTS FOR THIS CYBER SECURITY INCIDENT
In response to consumer inquiries, we have made it clear that the arbitration clause and class action waiver included in the Equifax and TrustedID Premier terms of use does not apply to this cybersecurity incident.”
They made it clear because “customers” were up in arms and it was not clear before.
When logging into the site and checking your status it was not clear whether or not you had been affected. What?!? They rolled out a specific site to let you see if you were affected and then it didn’t tell you whether or not you were? I didn’t know when I tried it for myself. But I guess now you can trust them because it totally works and stuff:
” YOU CAN DETERMINE YOUR STATUS IMMEDIATELY
Some consumers who visited the website soon after its launch failed to receive confirmation clarifying whether or not they were potentially impacted. That issue is now resolved, and we encourage those consumers to revisit the site to receive a response that clarifies their status.”
Which meant that their call centers were probably flooded…
“EXPANDED OUR CALL CENTER
We have tripled our call center team to over 2000 agents and continue to add agents.Our goal is to make this process as convenient and consistent as possible. We will continue to identify steps to improve this process.”
Then it came to light that the site created to check whether or not you are affected was not using the latest and greatest in cyber security technology. And was using a stock version of WordPress. And had a less than stellar security certificate. And the site wasn’t even registered to Equifax. The tech blog, ArsTechnica, covered this perfectly.
“What’s more, the website www.equifaxsecurity2017.com/, which Equifax created to notify people of the breach, is highly problematic for a variety of reasons. It runs on a stock installation WordPress, a content management system that doesn’t provide the enterprise-grade security required for a site that asks people to provide their last name and all but three digits of their Social Security number. The TLS certificate doesn’t perform proper revocation checks. Worse still, the domain name isn’t registered to Equifax, and its format looks like precisely the kind of thing a criminal operation might use to steal people’s details. It’s no surprise that Cisco-owned Open DNS was blocking access to the site and warning it was a suspected phishing threat.
Another indications of sloppiness: a username for administering the site has been left in a page that was hosted here.”
Here is the thing. The state of corporate America today and the out-for-blood societal reactions (some could argue that this is just such a reaction) have made it necessary to plan for catastrophic events in advance, even simulate responses to sharpen skills. The harsh reality is that if there is a major event, every action the company takes will be closely watched and scrutinized, fairly or unfairly. This exact case should have been one of their disaster scenarios. If you run an airline, you should have a plan in place in the event of an aircraft crash or hijacking. It’s unpleasant to think about, but it’s the business they are in. If you run a bank, you ought to have something ready in the case of a bank robbery, a run on the bank or liquidity issues.
It seems like Equifax did have a plan but either followed it terribly or didn’t take it seriously enough to think it could happen to them. Setting up a WordPress site and requiring potentially affected customers to give limited portions of sensitive information was a bad plan.
I haven’t seen anyone ask the question yet (though I could have missed it) you I will pose it here: If only 209,000 were affected why not contact them individually? Send an email, or place a phone call along with some verifiable security measures, that inform the affected that their information could be compromised, what they intend to do about it and what consumers should know. Why not already set up the identity protection for them in advance? Protect them first while the details are sorted out.
Meanwhile, I am over here filing a dispute to the same system they knew had been the source of the breach and I know nothing about it though Equifax had for several weeks. That’s bush league at best.
Tone-Deaf and Flat-Footed
I am not one to call for CEOs to get canned over events that happen at their organization – they can’t be everywhere all the time. I am one, however, to judge them on their response. When the Dr. Dao incident happened at United, I didn’t even blame CEO Oscar Muñoz for his initial response though he should have looked at the evidence first. People get bumped from airplanes all the time, some of them do not understand the contract of carriage and that the airline has a right to oversell a plane, and that customers accept the right of the airline to involuntarily deny boarding. His response seemed in line with the public reaction to that policy before he knew the whole extent of the matter. If anything, his reaction was far too quick and that is where I saw room for improvement.
Looking at the reaction to this event, leadership at Equifax had so many blunders it’s no wonder they were caught asleep at the wheel. When your business is holding people’s most sensitive information, your focus should be built around security. But Equifax (along with the other bureaus) would no doubt be a high value target for constant attacks from nefarious hackers. So plan, and execute when the plan goes south. Instead it came off as flat-footed.
Instead, leadership sold off $1.8MM in sharesafter the Equifax (though before these specific executives) knew of the problem and began their investigation but before the news was announced to the public causing a likely drop in the stock price. One thing to note about public companies, some executives that hold certain classes of shares are required to plan their asset sales well in advance. This was not such a sale. Assuming these three executives truly didn’t know about the breach and couldn’t be informed for security reasons, but were senior enough for these holdings to constitute a “small” portion of their holdings – buy the shares back! In a situation like this – optics matter. The optics on the stock sale loom large as it suggests that they had time and foresight to protect themselves when they didn’t seem to have time to protect the identities of millions of Americans.
The timeline is what really tells the story of Equifax’s poor approach and tone-deaf manner in this breach. The attack took place over several 8-10 weeks. Their investigation took another few weeks while they prepared their response simultaneously. Then the announcement comes and still delays affected customers by more than a week just from registering for the free protection that they could have turned on immediately?
Finally, someone should really consider starting a crisis management social media team to come in and take over for companies that experience disasters like this. The Equifax twitter approach is the definition of tone deaf.
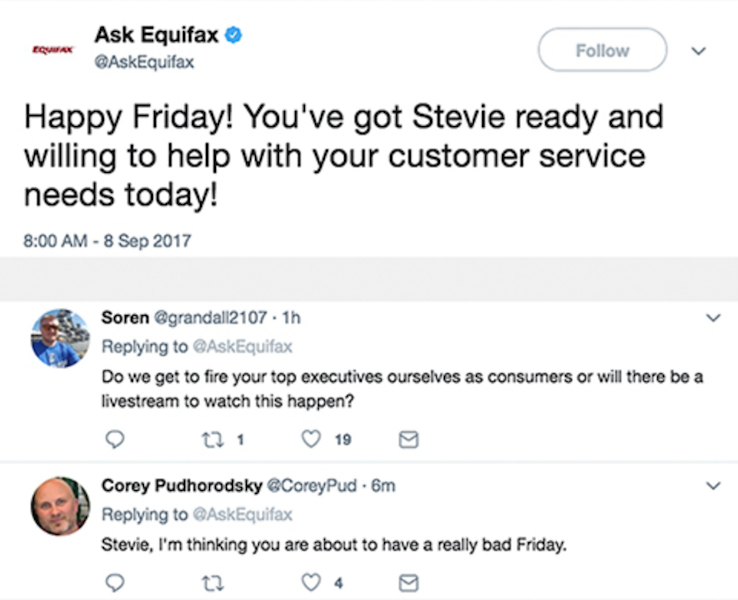
Bad things happen to good companies. It’s their response that matters in these situations, and Equifax looked like a very small company caught in a very big mess. They are entrusted with the most sensitive data a person possesses, and they seemed completely unprepared despite weeks of planning and notice.
What do you think about their handling of the situation? Were you an affected party?



Every computer science professor I talked to opined this incident looks like an inside job hack. How come no termination announcements were made holding a department or individuals responsible?
Well if no one else, their marketing department deserves a pretty hard look regardless of who is responsible for the actual attack. Their response would have been laughable it wasn’t such a serious matter.
Also, in the original terms-of-use, by signing up for Equifax’s credit monitoring you could end up waiving your right to sue. Thankfully the company has amended that with pressure from the NY AG.
https://arstechnica.com/tech-policy/2017/09/are-you-an-equifax-breach-victim-you-must-give-up-right-to-sue-to-find-out/
Agreed. That was sloppy and sneaky.
Add to all of this, several senior executives sold stock before the public announcement. I hope the SEC starts investigating those stock sales immediately. Their response has been incredibly disappointing.
That stock sale is linked in the post, but here is a quick link to a Bloomberg article outlining it: https://bloom.bg/2wSRV89. I initially thought it was nefarious but the company reports it was benign and those executives had no knowledge. It’s possible, but I am sure the regulators and interested authorities will dig a little deeper into it anyway.
I must be missing something. I’m I to understand that is totally acceptable to you to beat up a PAYING CUSTOMER for the failure of employees in the performance of their duties?
I’m not sure I understand your comment.
“When the Dr. Dao incident happened at United, I didn’t even blame CEO Oscar Muñoz for his initial response though he should have looked at the evidence first. People get bumped from airplanes all the time, some of them do not understand the contract of carriage and that the airline has a right to oversell a plane, and that customers accept the right of the airline to involuntarily deny boarding. His response seemed in line with the public reaction to that policy before he knew the whole extent of the matter. ”
People are beaten up all the time when they get bumped of a flight?
He had been seated on the plane; doesn’t that physically preclude the denial of boarding concept?
What I gather from the excerpt on which you talk about the “contract of carriage” is that you believe that a seated paying customer (Dr.Dao), deserved the treatment that he got due to the failure of the flight attendants to anticipated or react to the situation with more pro active measures to remedy the situation. You also seem to believe that the public shares your opinion on the matter. You forget that contract of carriage or not Dr. Dado PAID for a service, and to many people, ( including you), some one else’s failure to do their job would be immaterial to exercise their rights to the services to which they paid.
Based on some of your previous writings, I don’t believe that my take away is consistent with the picture of the kind of person I believe you to be. So that is why asked: did I miss something?
I will let Kyle speak for himself
But I’m curious. Are you upset because United excercised their legal right to remove Dr. Dao from the flight? Or are you upset because the CPD injured him in the course of his removal? You do know these two disparate events while linked are the responsibility of different parties right?
I’m also curious how you view Dr. Dao’s responsibility in all this? Was it ok for him to stubbornly sit there as the cops repeatedly warned him that if he didn’t get up he would be arrested and forcibly removed from the flight?
I addressed Robert’s question, but still wanted to weigh in on this. I agree that these were not UA employees. Once they had made the offer and indicated that in lieu of anyone accepting the offer that the next course was to remove the passenger fitting their contract of carriage (last to checkin or whatever) then they followed their next protocol, getting the authorities involved. I don’t think that UA employees were necessarily to blame, I think that most of this falls on the shoulders of Dr. Dao and the authorities, but I don’t think the agents for United were actually wrong in their process or approach.
I was speaking more to the fact that CEO Muñoz response before the info had come out was probably not the best, but with the information he had, I don’t know that he could be blamed for his standard reaction.
I appreciate the clarification on your question and allowing me to clarify what I put in the post and my intention. I was speaking to CEO Muñoz very initial reaction before the video (the evidence I referenced) had come to his attention. I have found a decent post from the New York Times (http://nyti.ms/2xfPo8k) which chronicles the timeline. His initial response based solely on his employee accounts before the videos surfaced was as follows:
My point was not that it’s ok to react in the way that Chicago authorities did in the matter. Those were not UA employees anyway and they were acting on their own accord. Rather it was to say that without the videos he heard a report from his employees, knew it was gaining attention, was asked to comment and issued a boiler plate response. I don’t blame him for that even though he should have perhaps waited for more detail before reacting. If the CEO of IHOP is asked to comment about a customer complaint of hair in their food with his employees following their procedures, they may comment the same way. If a video surfaces on the internet later showing a handful of 10″ strands baked into a pancake, then the reaction would (and should) differ.
What I fail to understand more than anything is why affected customers are forced to wait to sign up for identity protection on a schedule as determined by Equifax. So they mess up and put you at significant risk for identity theft and all the hassles associated with it, yet you can only protect yourself on a timeline of Equifax’s convenience? Dumb…
Just unthinkable.
You need to read the information this incident more carefully. You state “If only 209,000 customers were possible affected, why are 143 million at risk?”. That has been answered many times over in the general press. 209,000 people potentially had detailed credit card information stolen (presumably the information they used to purchase credit reports or credit monitoring services, but that’s a guess on my part) but 143 million people potentially had their SSNs, birth dates, etc stolen. All 143 Million need to be concerned.
See this link: https://www.consumer.ftc.gov/blog/2017/09/equifax-data-breach-what-do
I should have rephrased to suggest that serious exposure is likely limited to a much smaller group than the balance of their database.
Please contact me regarding an American Express data breach that the company has ignored.
I need your email address as I am not on social media.
I’ve received your email.